How Trusted Integrations Became the Perfect Attack Vector
.png)
.png)
A technical deep-dive into the anatomy of API-driven attacks and the security paradigm that could have prevented them
The most dangerous attacks don't break down your front door, they walk through it with a smile and a badge that says "authorized."
I want to tell you about an attack that should fundamentally change how you think about cybersecurity. Not because of its technical complexity, though the elegance was undeniable, but because of how it exploited the very foundation of modern business: trust. This is the story of how the integrations that make your organization more efficient became the perfect weapon against you, and why every security strategy built on perimeter thinking is already obsolete.
The future of cyber warfare isn't about sophisticated malware or exotic exploits. It's about understanding your digital ecosystem better than you do, and using that knowledge to make theft look like business as usual.
The Perfect Crime: When Trust Becomes Vulnerability
Picture this: Your organization's crown jewels - customer data, financial records, intellectual property - protected by layers of security. Firewalls, intrusion detection, multi-factor authentication. You've checked every box the consultants recommended. You're compliant with every framework that matters.
And then, one morning, you discover that millions of customer records have walked out the front door. Not through some exotic zero-day exploit or sophisticated malware, but through the very integrations you trusted to make your business more efficient.
This isn't hypothetical. This exact scenario has played out across major enterprises, with attackers leveraging OAuth tokens from legitimate third-party integrations - Salesloft, Drift, the productivity tools your sales team depends on - to systematically exfiltrate sensitive data from Salesforce instances. The beautiful irony? The attack traffic looked identical to legitimate business operations.
Dissecting the Attack
Let me walk you through how this unfolded—because understanding the anatomy of failure is the first step toward building something better.
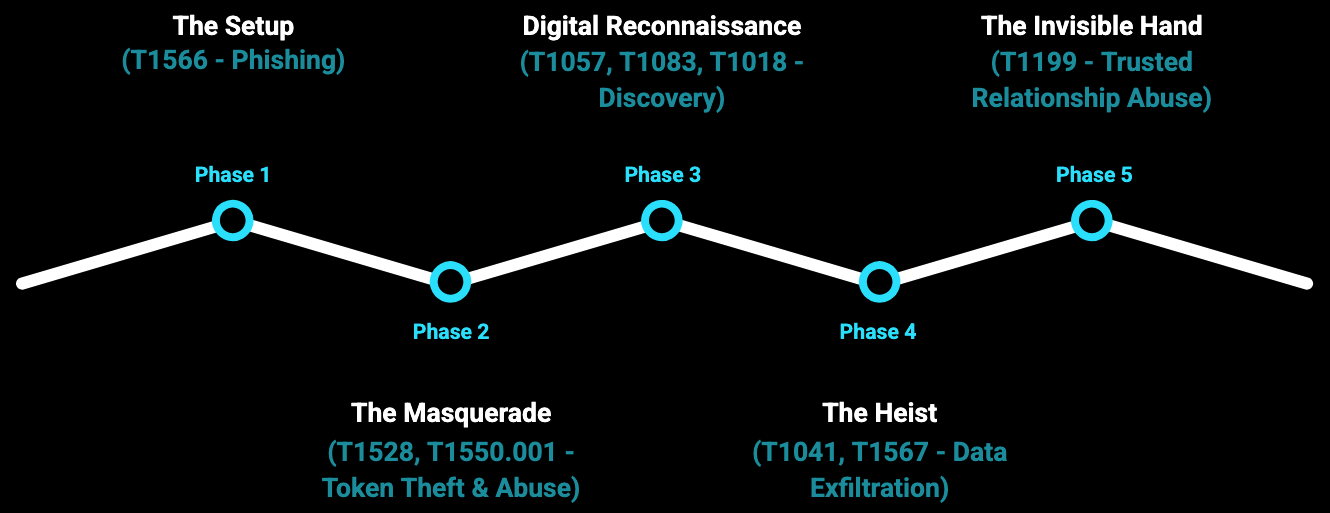
Phase 1: The Setup(T1566 - Phishing) It started with phishing, as these stories often do. But here's where it gets interesting - the attackers weren't after passwords. They were after something far more valuable: OAuth tokens. These digital keys that applications use to authenticate with each other, bypassing traditional security controls like MFA entirely.
Phase 2: The Masquerade(T1528, T1550.001 - Token Theft & Abuse) Once they had legitimate OAuth tokens from Salesloft and Drift integrations, the attackers had achieved something remarkable, they looked exactly like trusted business applications. No suspicious IP addresses. No abnormal authentication patterns. Just legitimate API traffic from authorized integrations.
Phase 3: Digital Reconnaissance(T1057, T1083, T1018 - Discovery) Before moving to exfiltration, they performed systematic reconnaissance. SOQL queries to understand data structures, API endpoints to map available resources, careful enumeration of what they could access. All of this appeared as normal integration behavior to traditional security tools.
Phase 4: The Heist(T1041, T1567 - Data Exfiltration) Finally, the payload. Systematic extraction of Lead, Contact, and Account data, including custom objects containing the most sensitive information. Names, emails, phone numbers, and whatever other PII these organizations had accumulated. All flowing through legitimate API channels.
Phase 5: The Invisible Hand(T1199 - Trusted Relationship Abuse) The masterstroke? This entire operation leveraged trusted relationships. No traditional security tool flagged it because the access came from authorized integrations. The perfect crime, executed in plain sight.
The Fundamental Problem: Security for a World That No Longer Exists
Here's what should keep you awake at night: your current security stack was designed for a perimeter-based world. Applications lived in data centers. Traffic flowed through predictable chokepoints. Trust was binary, you were either inside the network or outside.
That world is dead.
Today's applications are API-first, cloud-native, and built on a web of interconnected services. Your "perimeter" now includes every SaaS integration, every third-party service, every OAuth relationship your organization has established. And traditional security tools such as WAFs, firewalls, even most SIEM solutions, are fundamentally blind to the context that matters in this new reality.
The Solution: Context-Aware API Security
This is where the story gets interesting, because there is a solution. Not an incremental improvement to existing approaches, but a fundamental paradigm shift. Let me show you how Traceable's approach would have detected, prevented, and contained this attack at every phase.

Detection: Behavioral Baselines and Anomaly Recognition
Traceable's platform doesn't just monitor API traffic, it understands it. Every OAuth token has a behavioral profile. Every integration has established patterns. When those patterns deviate, the system knows.
OAuth Token Abuse Detection: The moment those compromised tokens started behaving differently - accessing APIs outside their normal scope, generating queries unlike typical integration patterns - Traceable would have flagged it.
Reconnaissance Pattern Recognition: Those systematic SOQL queries? They would have triggered behavioral alerts. The platform's machine learning engine would have recognized the difference between normal business logic and systematic data exploration.
Context-Aware Analysis: Unlike traditional tools that see individual API calls in isolation, Traceable correlates every transaction across time, building a complete picture of user behavior and system interaction.
Prevention: Real-Time Threat Mitigation
But detection is only half the equation. The real value lies in prevention, stopping attacks before they achieve their objectives.
Immediate Alert and Response: When suspicious OAuth behavior is detected, the system triggers immediate alerts to security teams with detailed context about the anomalous activity, enabling rapid manual intervention to revoke compromised tokens.
Sensitive Data Protection: Traceable tracks data flows end-to-end. When PII starts moving in patterns that deviate from normal business operations, the system can block the transfer automatically.
Business Logic Enforcement: The platform understands not just what data is being accessed, but whether that access makes sense in the context of normal business operations.
Containment: Comprehensive Incident Response
When an attack is detected, speed of response determines the scope of damage. This is where Traceable's API Data Lake becomes invaluable.
Complete Transaction History: Every API call, every request, every response; captured and available for forensic analysis. No guesswork about what data was accessed or when.
Impact Assessment: Precise determination of what was compromised, which systems were affected, and what data needs to be considered breached.
IOC Integration and Threat Hunting: When threat intelligence is published, the platform can correlate indicators against months of historical data, identifying related incidents and preventing future attacks.
The Data Advantage: Why Context Is Everything
Here's what sets this approach apart: it's not just about collecting more data, it's about understanding the relationships between data points. Traceable's platform captures not just the what, but the who, when, how, and why of every API interaction.
This context enables the platform to distinguish between legitimate business activity and subtle abuse of trusted relationships. It's the difference between a motion detector that triggers on every shadow and an intelligent system that understands the difference between a cat and a burglar.
The Future Is API-First
This isn't a trend you can wait out. APIs have become the primary interface for how applications communicate, how data flows between systems, how business gets done. The attack I described represents just the beginning of what's possible when adversaries understand your infrastructure better than you do.
The question isn't whether you'll face API-driven attacks. The question is whether you'll be prepared when they arrive.
MITRE ATT&CK Ref.
A step-by-step breakdown of the techniques used in the breach, and how Traceable's context-aware platform transforms every one into a detection opportunity.

The Inside Trace
Subscribe for expert insights on application security.
.avif)




